STUN 프로토콜
- RFC 3489: STUN - Simple Traversal of User Datagram Protocol (UDP) Through Network Address Translators (NATs)
- RFC 5389: Session Traversal Utilities for NAT (STUN)
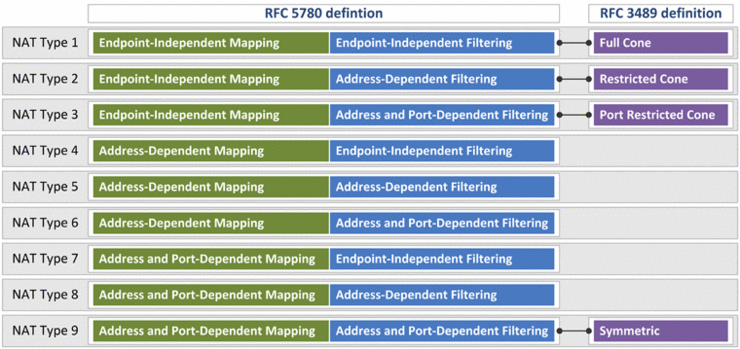
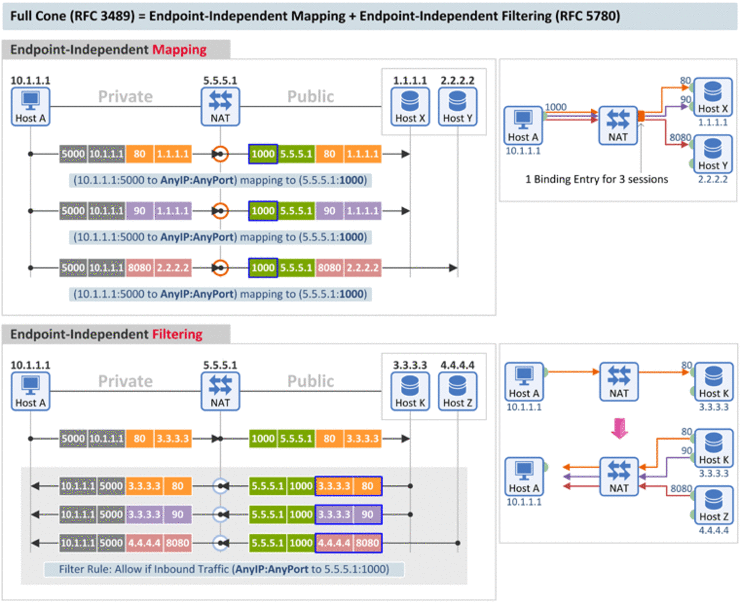
[Mapping Behavior] A full cone NAT is one where all requests from the same internal IP address and port are mapped to the same external IP address and port. [Filtering Behavior] Furthermore, any external host can send a packet to the internal host, by sending a packet to the mapped external address. (RFC 3489) |
- Mapping Behavior: Outbound 패킷의 (1) Source IP, (2) Source Port만 동일하다면 Destination IP, Destination Port에 상관없이 같은 Port Mapping 값(Translated Port = 1000)을 사용
- Filtering Behavior: Inbound 패킷에 대해 (1) Destination IP, (2) Destination Port만 검사하여 패킷의 허용 여부를 판단하고, External Endpoint의 소스 정보 즉, Source IP와 Source Port 값은 상관하지 않음
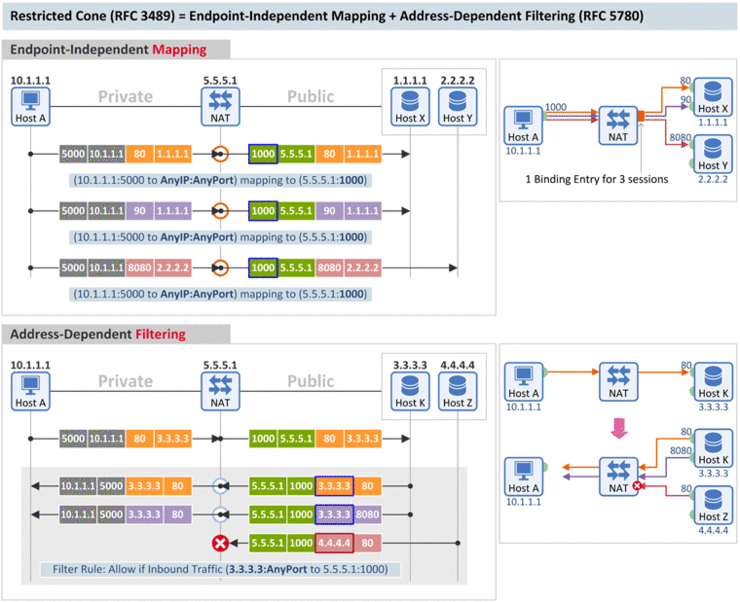
[Mapping Behavior] A restricted cone NAT is one where all requests from the same internal IP address and port are mapped to the same external IP address and port. [Filtering Behavior] Unlike a full cone NAT, an external host (with IP address X) can send a packet to the internal host only if the internal host had previously sent a packet to IP address X. (RFC 3489) |
- Mapping Behavior: Full Con과 동일
- Filtering Behavior: Inbound 패킷에 대해 (1) Destination IP, (2) Destination Port 그리고 (3) Source IP를 검사하여 패킷의 허용 여부를 판단하고, External Endpoint의 Source Port 값은 상관하지 않음
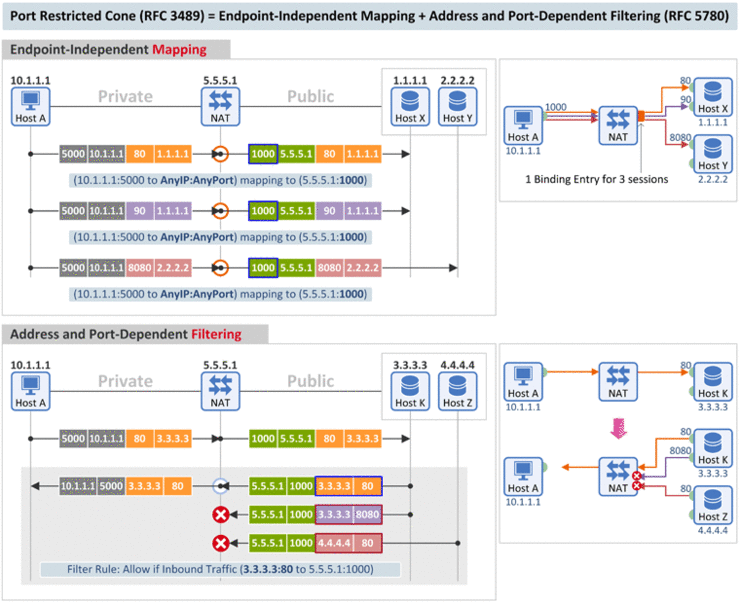
[Mapping Behavior] A port restricted cone NAT is like a restricted cone NAT, [Filtering Behavior] but the restriction includes port numbers. Specifically, an external host can send a packet, with source IP address X and source port P, to the internal host only if the internal host had previously sent a packet to IP address X and port P. (RFC 3489) |
- Mapping Behavior: Full Con과 동일
- Filtering Behavior: Inbound 패킷에 대해 (1) Destination IP, (2) Destination Port 그리고 (3) Source IP, (4) Source Port를 검사하여 패킷의 허용 여부를 판단함
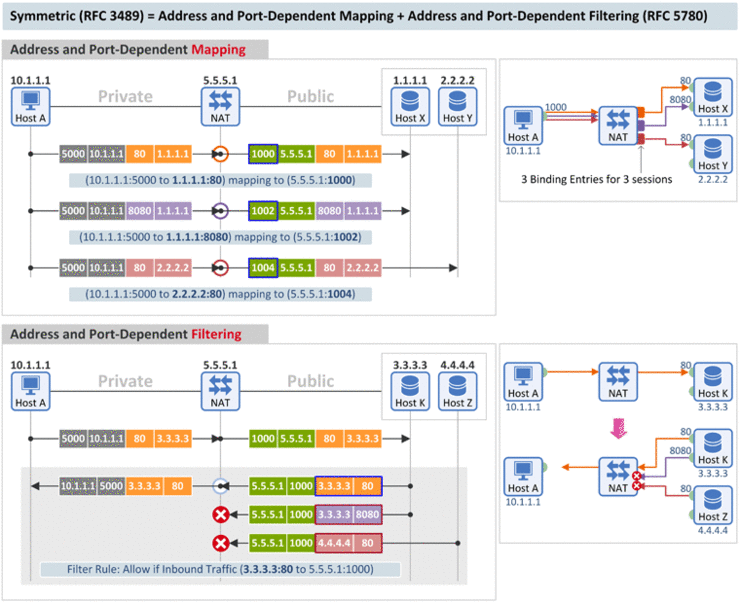
[Mapping Behavior] A symmetric NAT is one where all requests from the same internal IP address and port, to a specific destination IP address and port, are mapped to the same external IP address and port. If the same host sends a packet with the same source address and port, but to a different destination, a different mapping is used. [Filtering Behavior] Furthermore, only the external host that receives a packet can send a UDP packet back to the internal host. (RFC 3489) |
- Mapping Behavior: Outbound 패킷의 (1) Source IP, (2) Source Port 그리고 (3) Destination IP, (4) Destination Port가 모두 동일해야 같은 Port Mapping 값을 사용
- Filtering Behavior: Port Restricted Con과 동일